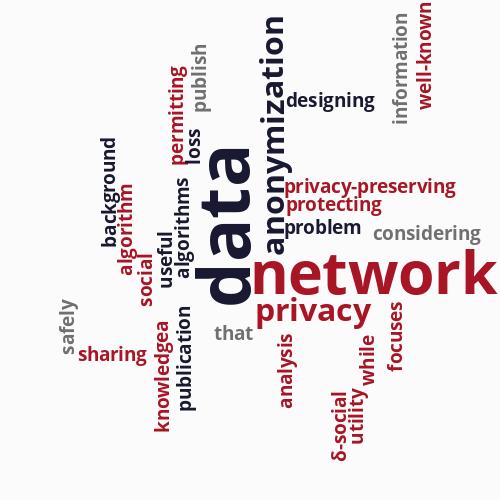
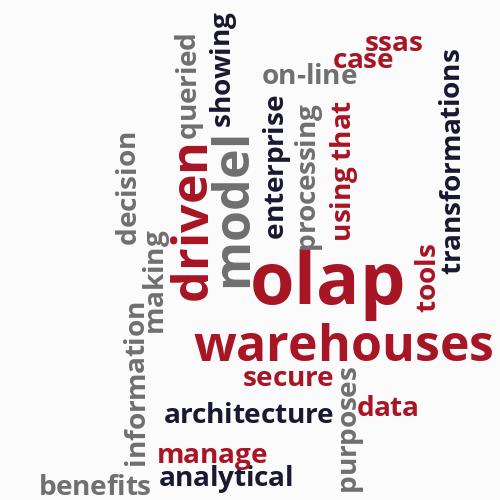
79 items matching your criteria
Sort by:
Research Article
01-03-2015
Unique: 525 | Total: 675
369-383
Research Article
01-02-2015
Unique: 423 | Total: 519
268-305
Research Article
01-03-2014
Unique: 508 | Total: 703
385-405
Research Article
01-02-2014
Unique: 639 | Total: 880
79-106
Research Article
01-09-2013
Unique: 512 | Total: 668
2241-2265
Research Article
01-12-2012
Unique: 537 | Total: 674
2920-3006
Research Article
28-06-2012
Unique: 510 | Total: 631
1741-1756
Research Article
28-06-2012
Unique: 448 | Total: 580
1703-1720
Research Article
28-06-2012
Unique: 512 | Total: 690
1643-1661
Research Article
28-06-2012
Unique: 497 | Total: 670
1608-1627
Research Article
01-06-2012
Unique: 491 | Total: 643
1558-1575
Research Article
01-05-2012
Unique: 474 | Total: 599
1112-1131
This website uses cookies in order to improve your web experience. Read our Cookies Policy